
Understanding the Digital Immune System in Cybersecurity
Cybersecurity pros are championing a new approach to cybersecurity – a digital immune system (DIS) – a proactive methodology that anticipates and adapts to evolving threats. Inspired by the remarkable resilience of the human immune system, a digital immune system in network security aims to provide a proactive and dynamic defense against cyber threats. It’s not a single technology, but rather a holistic approach that integrates various practices and technologies throughout the software development lifecycle, from design to operations.
As our digital landscape gets more expansive and cemented into our daily regimen of work, the threats we face alongside it continue to evolve. With the speed of change, traditional security measures are often reactive and struggle to keep pace with the ever-increasing sophistication of cyberattacks.
Here’s how to start your own.
What is a digital immune system?
A Digital Immune System is a cybersecurity framework designed to protect digital networks by continuously monitoring, identifying, and responding to potential threats. The core idea behind digital immunity is to provide a robust defense that not only reacts to attacks but also evolves with the threat landscape. A DIS integrates various technologies, such as artificial intelligence (AI), machine learning (ML), automation, and analytics, to create an adaptive cybersecurity environment. This system improves over time by learning from past incidents and continuously updating itself to safeguard against new, more sophisticated attacks.
Digital immunity is crucial for preventing, detecting, and responding to cyber threats in real-time. As cyber threats become more advanced and persistent, traditional reactive approaches are no longer sufficient. A DIS takes a proactive stance, minimizing risks, improving resilience, and ensuring business continuity by acting as an intelligent and evolving shield against cyberattacks. It provides organizations with a dynamic and forward-thinking security solution capable of staying ahead of emerging threats.
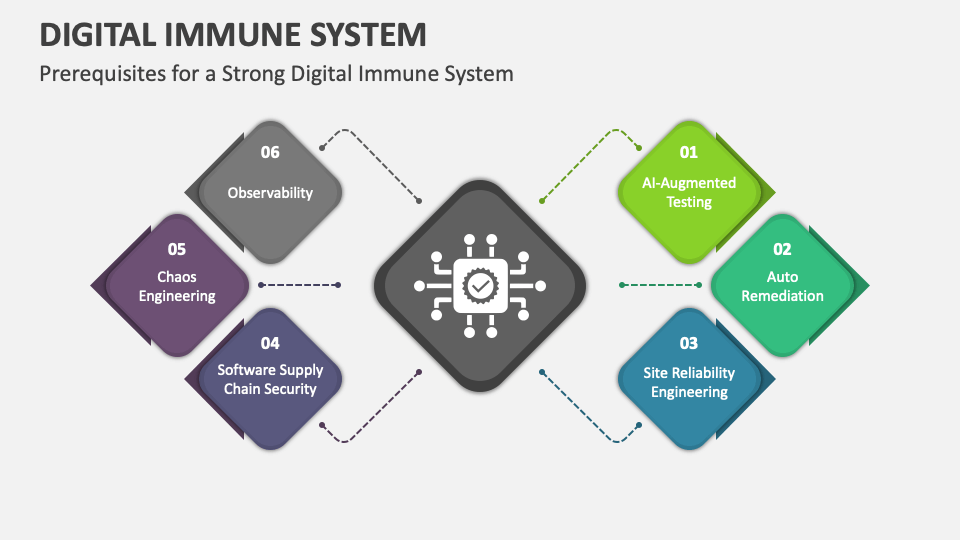
The pillars of a digital immune system
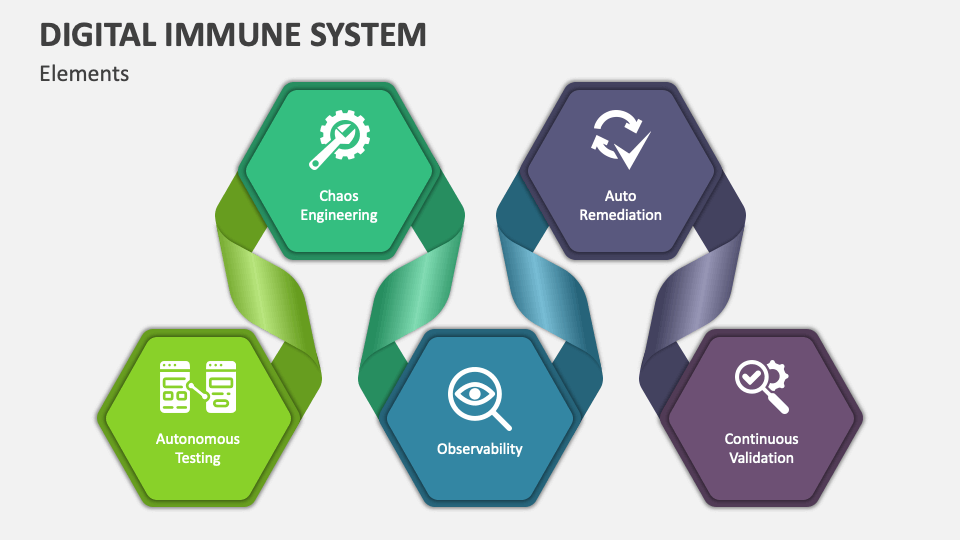
A DIS leverages existing security tools and platforms, such as intrusion detection systems (IDS) (systems that monitor network traffic for suspicious activity), and security information and event management (SIEM) (tools that collect and analyse security data from various sources), and endpoint protection solutions. This integration creates a unified defense network that shares information and coordinates responses, amplifying the effectiveness of each individual tool. In addition, a DIS is founded on the following pillars:
Continuous threat detection
A DIS acts as a vigilant sentinel, constantly monitoring the digital environment for anomalies and suspicious activity. This includes analysing network traffic, system logs, and application behaviour to identify potential threats in real-time. Machine learning and artificial intelligence play a crucial role in this process, allowing the system to learn and adapt to new attack vectors.
Automated response and mitigation
Once a threat is detected, a DIS should ideally be able to take immediate action to contain and neutralize it. This could involve automatically isolating infected systems, patching vulnerabilities, or deploying countermeasures to mitigate the attack. The key is speed and precision, minimizing the window of opportunity for attackers.
Self-learning and adaptation
A DIS is not static – it continuously learns and evolves. By analyzing past attacks and their outcomes, the system can refine its detection and response capabilities. This dynamic adaptation allows the DIS to stay ahead of the curve and respond effectively to even novel threats.
Integration with security tools: A DIS leverages existing security tools and platforms, such as intrusion detection systems (IDS) (systems that monitor network traffic for suspicious activity), and security information and event management (SIEM) (tools that collect and analyse security data from various sources), and endpoint protection solutions. This integration creates a unified defense network that shares information and coordinates responses, amplifying the effectiveness of each individual tool.
The benefits of implementing a digital immune system
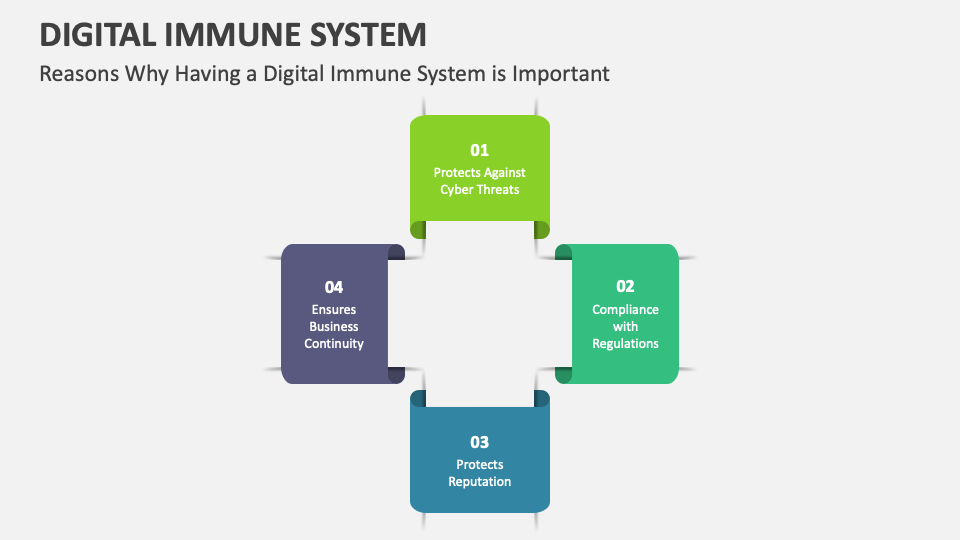
- Proactive defense: A DIS shifts the focus from reactive incident response to proactive threat prevention, significantly reducing the risk of successful attacks.
- Improved resilience: By automating responses and self-healing capabilities, a DIS minimizes downtime and data loss in the event of an attack.
- Reduced operational costs: Continuous monitoring and automated responses free up security teams to focus on strategic initiatives and investigations.
- Enhanced security posture: A DIS fosters a culture of security throughout the organization, embedding security considerations into every stage of the software development and deployment process.
Choosing the right platform
Several tech giants and platforms are actively involved in the development and implementation of digital immune systems.
Microsoft
Microsoft Azure Security Center is a comprehensive platform that offers features like continuous threat detection, vulnerability scanning, and automated remediation capabilities, aligning with the core principles of a DIS.
Google Cloud
Google Cloud Security Command Center (SCC) provides similar functionalities, including threat detection, incident response, and security automation. Google also invests heavily in AI and machine learning research, which are crucial for developing intelligent and adaptive DIS solutions.
IBM
IBM Security offers a range of products and services that contribute to a DIS, including X-Force Threat Intelligence, QRadar SIEM, and Resilient Incident Response Platform.
Palo Alto Networks
Palo Alto Networks Cortex XDR is a cloud-native platform that integrates threat detection, prevention, and response capabilities, aiming to provide a unified and automated approach to security.
CrowdStrike Falcon
This platform focuses on endpoint security and utilizes AI and machine learning to detect and respond to threats in real-time, contributing to the overall resilience of a digital ecosystem.
These are just a few examples, and the landscape is constantly evolving. Many other companies are developing and offering technologies and services that contribute to the DIS vision. It’s important to note that a DIS is not a single product or platform, but rather a holistic approach that requires the integration of various tools and practices. However, the platforms mentioned above provide valuable building blocks and functionalities that can be combined to create a comprehensive and effective DIS.
The digital immune system market and future trends
The DIS market is experiencing significant growth as businesses increasingly prioritize proactive cybersecurity measures. Market research shows the global DIS market at 25.30 billion USD in 2022 and is projected to grow at a compound annual growth rate (CAGR) of 12.7% from 2023 to 2030.
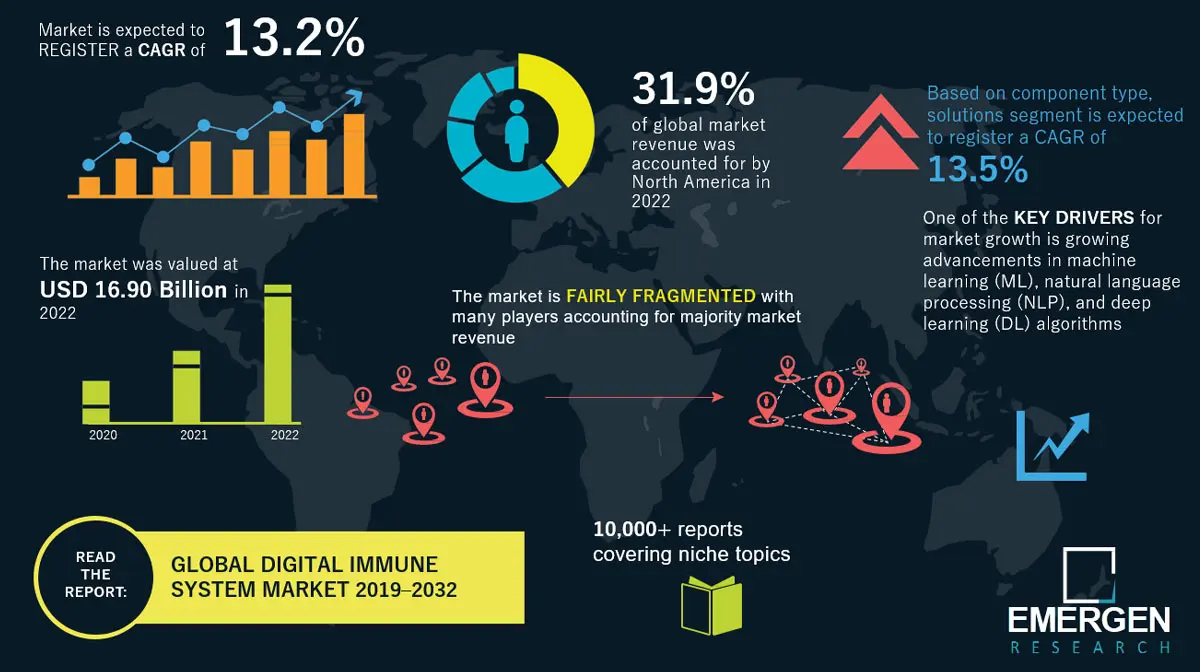
Industry trends around adoption of DIS and advanced cybersecurity frameworks are naturally aligned with industries that handle the most sensitive data: financial services, healthcare, and legal. As organizations continue to digitize and adopt remote work models, the demand for DIS solutions is set to rise across industries, ensuring digital immunity from potential cyber threats.
Looking ahead, the digital immune system market is expected to see further advancements with the integration of cutting-edge technologies. One of the key trends is the use of advanced AI models that enhance the ability of DIS frameworks to predict and counteract threats in real-time. AI will continue to refine the self-learning capabilities of digital immune systems, making them more adept at anticipating emerging threats based on evolving patterns.
Another promising innovation is the incorporation of blockchain technology into DIS frameworks. Blockchain’s decentralized and tamper-resistant structure can strengthen the integrity of cybersecurity defenses, ensuring more secure authentication and data validation processes. This development could significantly reduce vulnerabilities to hacking and fraud, making blockchain-enhanced DIS a game-changer in the cybersecurity landscape.
Implementing a DIS requires a significant shift in mindset and approach. Key challenges emerge when integrating various technologies and processes in a robust system with a single team. In addition, you need a master of data security in order to process the vast amount of data collected and analysed by a DIS necessitates robust data security measures to prevent unauthorized access and misuse. Balancing effective threat detection with minimizing false positives is crucial to avoid unnecessary disruption and resource drain.
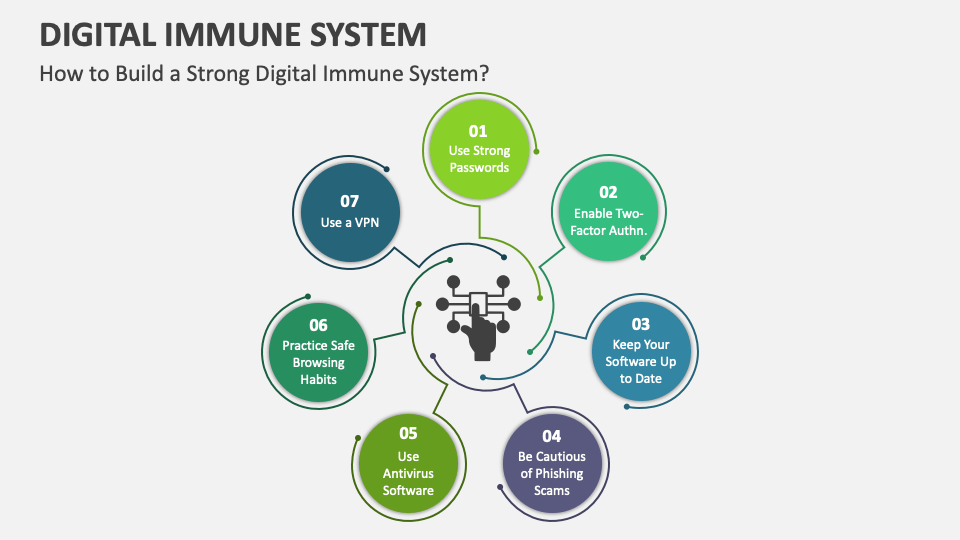
Distilled
The digital immune system represents a significant shift in cybersecurity, moving from reactive defense to proactive protection. By continuously monitoring, learning, and adapting, DIS solutions can significantly improve the resilience of digital infrastructure and provide a more secure future for organizations. As the technology landscape continues to evolve, the development and implementation of robust DIS solutions will be crucial for mitigating the ever-increasing threat of cyberattacks.