Quantum Security: Inside the Race to Reinvent Encryption
As quantum computers edge closer to reality, governments and tech giants rush to protect the world’s data before the locks fail.
Quantum computing has long been the stuff of sci-fi thrillers. But now, it’s inching closer to reshaping our digital defences. For decades, our security has relied on mathematical puzzles that computers can’t easily solve. Quantum machines, however, promise to change that. They could one day crack those puzzles faster than any supercomputer, putting the world’s encrypted data at risk.
That’s why governments, researchers, and tech giants are now leaning into Quantum Security, a new wave of defences built to withstand the coming quantum storm. With the US National Institute of Standards and Technology (NIST) rolling out its post-quantum cryptography (PQC) standards, the question isn’t if we need quantum-safe systems anymore, but how quickly we can make them
Let’s take a quantum leap and see where this journey begins.
Why quantum matters more than ever?
Today’s encryption methods, like RSA and elliptic-curve cryptography, depend on mathematical problems so hard that even powerful classical computers can’t solve them.
Quantum computers, however, change that equation. By using quantum bits, or qubits, these next-generation machines can process information in ways that feel almost otherworldly. They don’t just test one possible answer at a time; they explore many paths at once.
Algorithms like Shor’s take full advantage of that power, allowing quantum computers to factor huge numbers far faster than today’s machines ever could. In simpler terms, the locks that keep our digital lives safe, the encryption behind banking, messaging, and identity systems, could one day be picked in seconds.
And that’s not just a “someday” scenario. Security agencies are already warning about a new kind of threat known as “harvest now, decrypt later.” In this model, attackers quietly collect encrypted data today, waiting for the moment quantum computers become strong enough to crack it. When that happens, everything stored in those old vaults, financial records, medical data, private messages — could suddenly be exposed.
The rise of post-quantum cryptography
Enter post-quantum cryptography, or quantum-safe cryptography. Instead of relying on the mathematical traps that quantum computers can unravel, PQC uses completely new constructions, lattice-based, hash-based, and code-based algorithms that resist both classical and quantum attacks. After years of testing and public review, NIST released its first three Post-Quantum Cryptography Standards in August 2024. These include:
• ML-KEM (Module Lattice-based Key Encapsulation Mechanism), built on CRYSTALS-Kyber, for encrypting and sharing keys securely.
• ML-DSA (Module Lattice-based Digital Signature Algorithm), derived from CRYSTALS-Dilithium, for digital signatures.
• SLH-DSA (Stateless Hash-based Digital Signature Algorithm), from SPHINCS+, as a hash-based backup algorithm.
A few months later, In March 2025, NIST selected HQC (Hamming Quasi-Cyclic), a code-based scheme, to expand mathematical diversity and ensure long-term resilience. This moment marked a turning point: quantum security is no longer just a lab experiment. It’s entering the real world.
Where quantum security stands today?
You don’t need a quantum computer to use quantum-resistant tools. Organisations are already experimenting with hybrid encryption, blending classical cryptography with post-quantum algorithms for future-proof protection.
| Organisation / Project | Quantum Security Implementation | What It Means |
| Apple (PQ3 for iMessage) | Combines elliptic-curve and Kyber encryption | Enables quantum resistance in messaging without breaking compatibility |
| OpenSSL & WolfSSL | Testing PQC within TLS protocols | Prepares secure web traffic to withstand quantum-era attacks |
| liboqs / Open Quantum Safe | Open-source frameworks integrating PQC algorithms | Brings quantum-safe encryption to VPNs, authentication, and cloud systems |
| Performance Insights | PQC keys and signatures are larger but increasingly efficient | Shows PQC is viable for modern computing environments |
In short: quantum security isn’t on the horizon, it’s already here, quietly reshaping the tools that keep digital communication safe.
The growing pains
Transitioning to quantum-safe systems won’t be easy. Larger key sizes demand more bandwidth and storage, and smaller devices like phones and sensors may struggle. Migration adds another challenge, updating certificates, protocols, and firmware across global systems takes time and coordination. And even with NIST’s standards in place, experts agree on one thing: flexibility is key. The algorithms we trust today might not last forever, so building crypto agility, the ability to update defences without disruption, will decide who adapts fastest.
Why preparation matters right now?
Many executives assume they can wait until quantum computers become mainstream before acting. That’s a mistake. Because encrypted data can be stored indefinitely, sensitive information shared today, medical records, financial statements, and national security data, could be decrypted years later. The time to start transitioning is now.
Organisations should begin by auditing their cryptographic landscape. Identify which applications rely on vulnerable algorithms, prioritise high-value systems, and explore hybrid models that blend existing encryption with PQC. Adopting NIST’s PQC algorithms early provides an advantage. It builds resilience before the threat becomes existential.
The global shift toward quantum-safe infrastructure
The world isn’t waiting for quantum computers to arrive; it’s already preparing for them. From cloud systems to national frameworks, the race to build quantum-safe infrastructure is well underway.
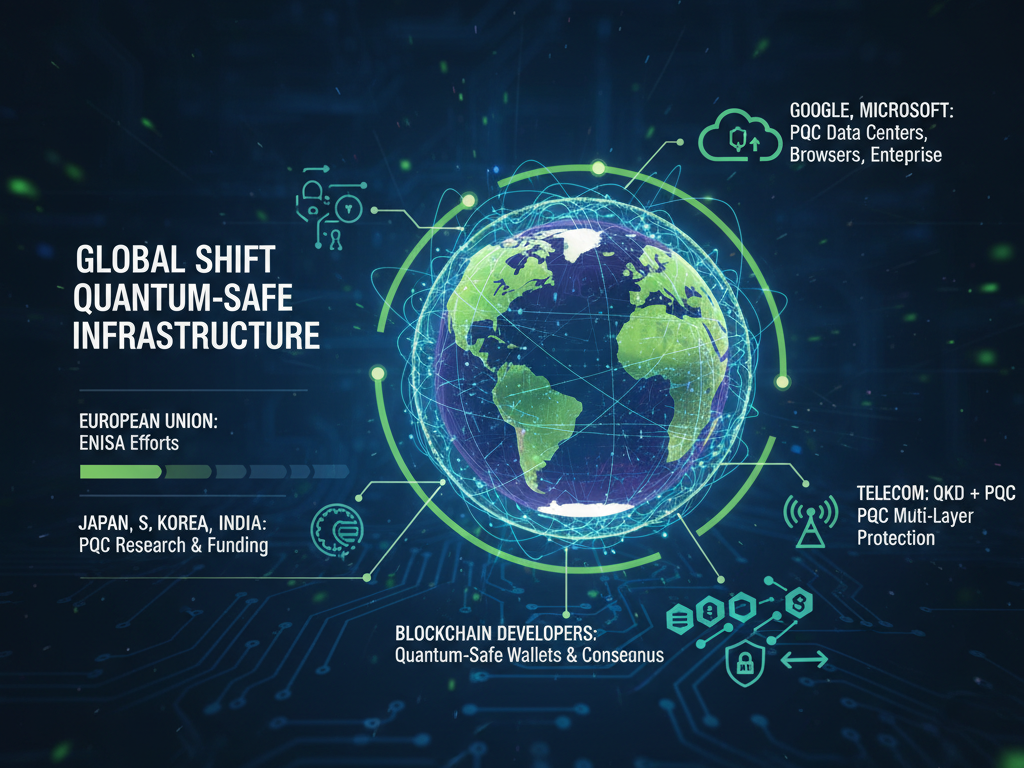
Across regions, the momentum is unmistakable:
- In Europe, the EU Agency for Cybersecurity (ENISA) is guiding a coordinated shift to post-quantum cryptography (PQC). The goal is simple, keep government and private systems secure long before quantum threats become real.
- Across Asia, countries like Japan, South Korea, and India are putting serious funding into PQC research and pilot projects. They’re building regional standards that can work hand-in-hand with the new NIST Post-Quantum Standards.
- Tech giants such as Google and Microsoft are already adapting their systems. They’re adding PQC protection to data centres, browsers, and enterprise tools, quietly building the backbone for a quantum-safe internet.
- Telecom networks are testing combinations of quantum key distribution (QKD) and PQC to layer security across global communication grids, the pipes that carry everything from personal calls to critical data.
- Blockchain developers are also joining in, designing quantum-safe wallets and rewriting consensus systems so that digital assets remain protected for decades to come.
This collective momentum shows that the shift to quantum-safe infrastructure is already in motion, a global collaboration redefining how the digital world prepares for its next great leap in security.
The next chapter of quantum security
The next five years will define whether quantum security becomes a universal standard or another tech buzzword. Expect rapid progress in hardware acceleration, software libraries, and integration tools. PQC-enabled VPNs, browsers, and cloud APIs will likely appear across mainstream platforms.
Startups, too, are innovating with quantum-safe platforms-as-a-service, helping enterprises migrate securely with automation and monitoring baked in. What’s clear is this: Quantum Security is evolving from theoretical to tactical. The organisations that adapt early will lead the next era of digital trust.
Distilled
Quantum computing isn’t science fiction anymore, and quantum security isn’t hype. NIST’s Post-Quantum Standards have given the industry a roadmap. PQC algorithms like ML-KEM and ML-DSA are already securing communication systems. The challenge now lies in scaling them responsibly. The transition will take time, but waiting isn’t an option. In a few years, protecting the past will depend on how we act today.